- Published on
Space pirate - Going Deeper
- Authors

- Name
- EternalCirco
- Github
- @Eternalcirno
Unzip pwn_sp_going_deeper.zip to reveal a binary.
Putting the binary into Ghidra shows the password as DRAEGER15th30n34nd0nly4dm1n15tr4t0R0fth15sp4c3cr4ft as seen in the image below:
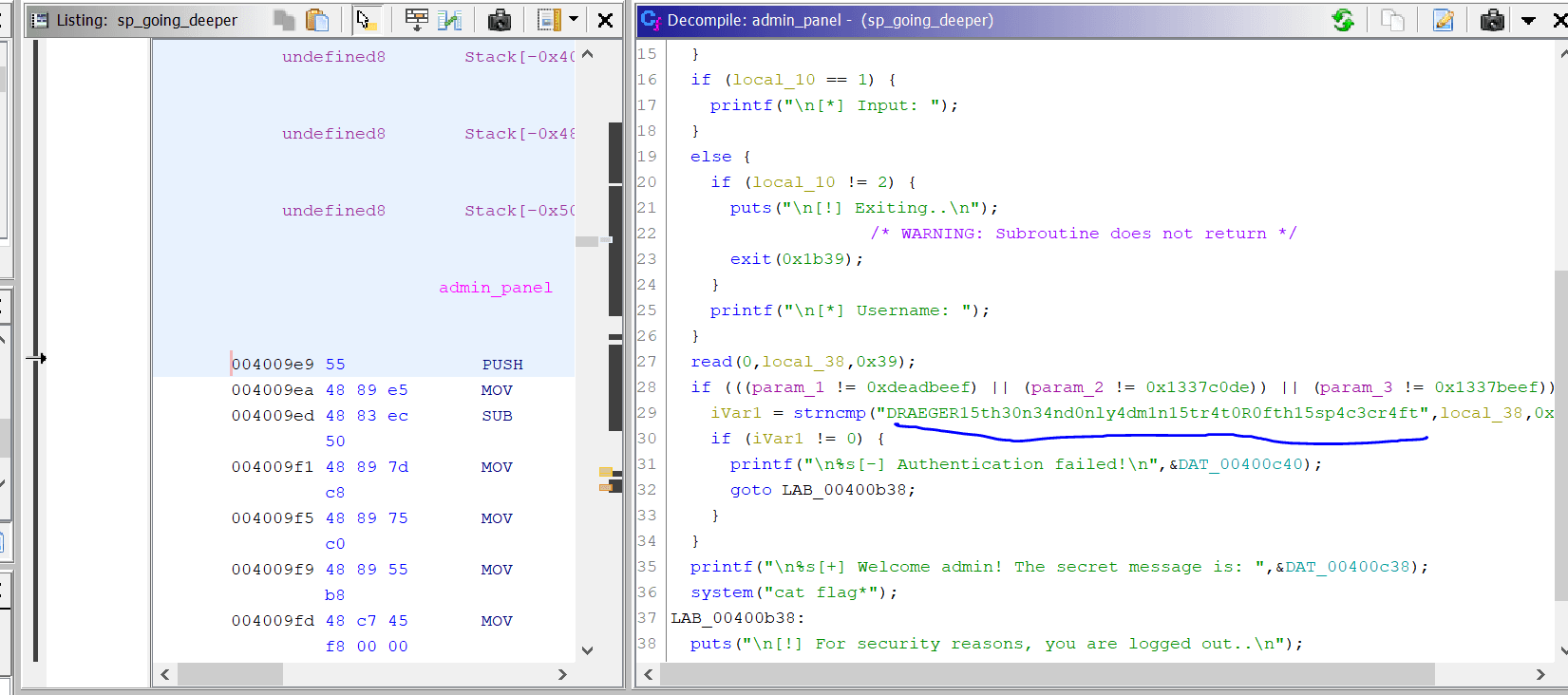
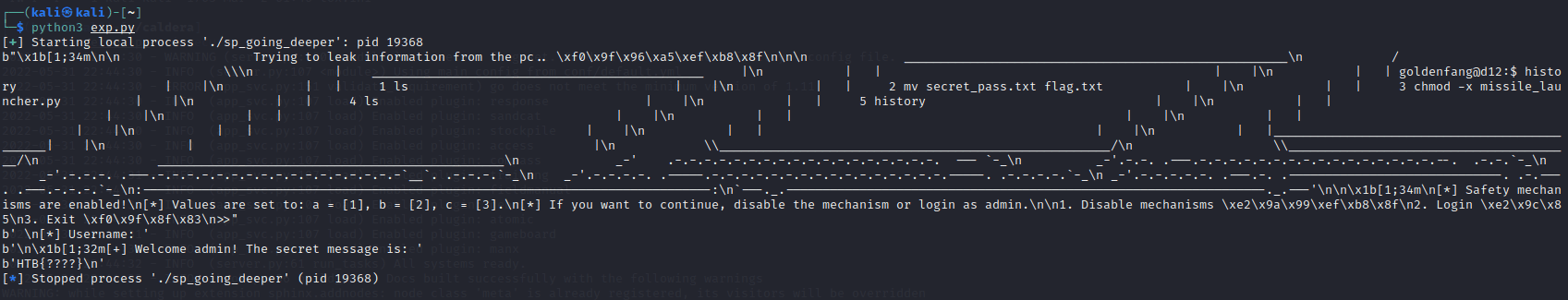
But since the LF char (0x0a) is taken into the input, strncmp() function call returns a non-zero result.
The exploit script is as follows; By terminating the string prematurely with a null byte, the LF char is not included and the strncmp() therefore returns 0, giving us the flag.